STAATSE — Cloud Security Services
Why is Cloud Security Important?
Cloud computing security is critical for most organizations today, as they increasingly rely on cloud services. Gartner predicted a 23.1% growth in the worldwide public cloud services market in 2021, reflecting the rapid adoption of these services.
As companies migrate to the cloud, understanding data security requirements is crucial. While third-party cloud providers manage infrastructure and follow best security practices, they aren’t solely responsible for data asset security and accountability. Businesses must take their own precautions to protect data, applications, and workloads in the cloud.
The evolving digital landscape brings more sophisticated security threats, many targeting cloud providers due to organizations’ limited visibility into data access and movement. Failing to enhance cloud computing security can expose organizations to significant governance and compliance risks when managing client information, regardless of its storage location.
Cloud security is a vital consideration for businesses of all sizes. With cloud infrastructure underpinning modern computing across industries, successful adoption hinges on implementing robust countermeasures against cyberattacks. Regardless of your company’s cloud type, employing cloud security solutions and best practices is essential for ensuring business success and continuity.
What is Meant by Cloud Security?
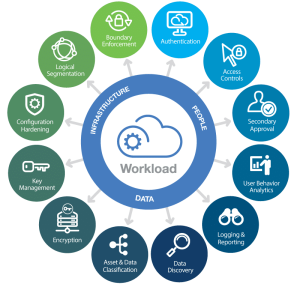
Cloud computing security, or cloud security, is a comprehensive set of policies, controls, procedures, and technologies working together to safeguard cloud-based systems, infrastructure, and data. These measures protect cloud data, ensure regulatory compliance, and maintain customer privacy. They also manage user and device authentication, control access to data and resources, and safeguard data privacy. Cloud security can shield a company’s data from various threats, including distributed denial of service attacks, malware, hackers, and unauthorized access.
Cloud security is customizable to meet specific business needs. Its centralized management reduces administrative overhead, freeing IT teams to focus on other business areas. The delivery of cloud security varies depending on the cloud provider or the implemented security solutions. Importantly, the implementation of cloud security processes is a shared responsibility between the business owner and the solution provider.
What Are the Four Areas of Cloud Security?
- Identity and Access Management (IAM): IAM tools enable enterprises to implement policy-driven protocols for users accessing on-premises or cloud-based services. Its core function is creating digital identities for all users, allowing active monitoring and restriction of their data interactions when necessary.
- Data Loss Prevention (DLP): DLP services ensure the security of regulated cloud data. These solutions employ remediation alerts, data encryption, and other preventive measures to protect data, both at rest and in transit.
- Security Information and Event Management (SIEM): SIEM offers a comprehensive security solution that automates threat monitoring, detection, and response in cloud environments. It uses AI-driven technologies to correlate log data across platforms and digital assets, enabling IT teams to apply network security protocols and respond swiftly to potential threats.
- Business Continuity and Disaster Recovery: Despite preventive measures, data breaches and outages can occur. Businesses must respond quickly to vulnerabilities or system outages. Disaster recovery solutions in cloud security offer the necessary tools, services, and protocols to recover lost data and resume normal operations.
STAATSE — Cloud Security Services
Cloud Security Risks
Cloud computing security risks typically fall into the following categories:
- Unauthorized access to internal data
- Malicious attacks (e.g., DDoS attacks or malware infections) that cripple or destroy cloud infrastructure
- Data leakage or exposure
- Excessive data access by authorized internal users
Cloud security aims to minimize these risks through encryption, user authentication, and other protective measures.
How Does STAATSE Provide Cloud Security?
Cloud security is a major concern for many businesses, which is why STAATSE offers comprehensive cloud computing security solutions. Our experts thoroughly analyze your cloud infrastructure to identify security vulnerabilities. Once these are found, we continue monitoring for other potential security issues during our assessments.We ensure that Identity and Access Management (IAM) settings and cloud infrastructure configurations are correctly implemented, preventing unauthorized public access. Our team diligently protects sensitive data, helping your business operate smoothly without the risk of security breaches.